IPv6 is another up coming trend on the internet. Since most of the ISPs do not provide the IPv6 service, how do we enjoy or experience the IPv6 benefit??
There are some IPv6 brokers on the internet that we can use IPv6 service over the existing IPv4 service. Some of the brokers are Hurricane Electric, Hinet, and etc….
There are some sample setup guide are already included in their website already, but their guide makes the SRX to route the IPv6 packets without policy restrictions capability. So I will attach mine as a reference for using IPv6 in flow mode.
| Syntax | definition |
|---|---|
| set security forwarding-options family inet6 mode flow-based | This command is to enable IPv6 support under the SRX. Although most of the sample config suggest to route mode, but we can use flow mode with 6in4. Applying this requires a reboot!!! |
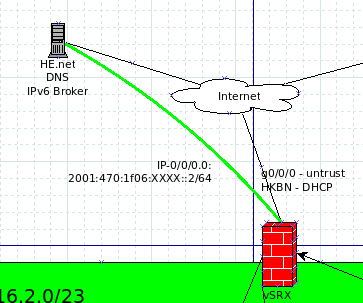
| set interfaces ip-0/0/0 unit 0 tunnel source 138.19.XXX.XXX set interfaces ip-0/0/0 unit 0 tunnel destination 209.51.161.14 set interfaces ip-0/0/0 unit 0 family inet6 address 2001:470:1f06:XXXX::2/64 |
The tunnel source is the SRX external IPv4 address. The destination is the HE.net IPv6 broker IPv4 address. The IPv6 address is the subnet used for the IP IP tunnel. |
| set interfaces ge-0/0/3 unit 0 description “guest vlan – 172.16.2.64/27” set interfaces ge-0/0/3 unit 0 family inet address 172.16.2.65/27 set interfaces ge-0/0/3 unit 0 family inet6 address 2001:470:1f07:XXXX::0041/123 |
The ge-0/0/3 is the interface for my guest vlan at home. This IPv6 address is using another route-able subnet provided by HE.net, and we can notice the different of this subnet is not part of the subnet that is being used in the IP IP tunnel. The tunnel is using 1f06, but the guest vlan is using 1f07 as highlighted in red. |
| set routing-options rib inet6.0 static route ::/0 next-hop 2001:470:1f06:XXXX::1 | This is the default route for inet.6, aka IPv6. However, the static route needs to be applied into the inet6.0 table, therefore we have to apply the static route under “rib inet6.0“. |
| set access address-assignment pool vlan36-Guest-pool-ipv6-pool family inet6 prefix 2001:470:1f07:XXXX::0040/123 set access address-assignment pool vlan36-Guest-pool-ipv6-pool family inet6 range vlan36-Guest-pool low 2001:470:1f07:XXXX::0043/128 set access address-assignment pool vlan36-Guest-pool-ipv6-pool family inet6 range vlan36-Guest-pool high 2001:470:1f07:XXXX::004f/128 set access address-assignment pool vlan36-Guest-pool-ipv6-pool family inet6 dhcp-attributes maximum-lease-time 120 set access address-assignment pool vlan36-Guest-pool-ipv6-pool family inet6 dhcp-attributes grace-period 3600 set access address-assignment pool vlan36-Guest-pool-ipv6-pool family inet6 dhcp-attributes dns-server 2001:4860:4860::8888 set access address-assignment pool vlan36-Guest-pool-ipv6-pool family inet6 dhcp-attributes dns-server 2001:4860:4860::8844set security zones security-zone guest interfaces ge-0/0/3.0 host-inbound-traffic system-services dhcpv6 |
This is the IPv6 DHCP setup for my guest vlan, and we have allowed the machines under guest zone to take obtain IPv6 addresses via DHCPv6 . |
| set security policies from-zone guest to-zone untrust policy 05-guest_to_untrust-icmp match source-address any set security policies from-zone guest to-zone untrust policy 05-guest_to_untrust-icmp match destination-address any set security policies from-zone guest to-zone untrust policy 05-guest_to_untrust-icmp match application junos-icmp6-all set security policies from-zone guest to-zone untrust policy 05-guest_to_untrust-icmp then permit set security policies from-zone guest to-zone untrust policy 05-guest_to_untrust-icmp then log session-init set security policies from-zone guest to-zone untrust policy 05-guest_to_untrust-icmp then log session-close |
This is a sample policy for IPv6. The any being used in both source and destination includes IPv4 and IPv6. |
| set security zones security-zone untrust interfaces ip-0/0/0.0 host-inbound-traffic system-services ping | This is to assign the IP-0/0/0.0 into the untrust zone. |
I have attached the snapshot of the traceroute to yahoo.com s IPv6 address. The latency of the traceroute is quite high since my SRX is in Hong Kong and the tunnel terminated in New York.
| traceroute to yahoo.com (2001:4998:58:1836::10) from 2001:470:1f07:XXXX::42, 30 hops max, 24 byte packets 1 2001:470:1f07:XXXX::41 9.41 ms 43.74 ms 12.935 ms 2 2001:470:1f07:XXXX::ffff:fffc 2.594 ms 13.369 ms 3.548 ms 3 2001:470:1f06:XXXX::1 260.973 ms 255.072 ms 250.282 ms 4 2001:470:0:5d::1 246.005 ms 245.525 ms 245.68 ms 5 2001:504:f::18 247.207 ms 302.59 ms 247.257 ms 6 2001:4998:f023:207:: 314.722 ms 266.338 ms 258.913 ms 7 2001:4998:f023:201::1 257.497 ms 277.118 ms 264.542 ms 8 2001:4998:124:fc05::1 259.676 ms 267.003 ms 258.725 ms 9 2001:4998:58:f809::1 271.751 ms 265.128 ms 260.707 ms 10 2001:4998:58:1836::10 265.884 ms 261.349 ms 260.75 ms |
The traceroute from SRX to yahoo.com IPv6.
| awong@SRX12-Gateway> traceroute no-resolve yahoo.com traceroute6: Warning: yahoo.com has multiple addresses; using 2001:4998:58:1836::10 traceroute6 to yahoo.com (2001:4998:58:1836::10) from 2001:470:1f06:XXXX::2, 64 hops max, 12 byte packets 1 2001:470:1f06:XXXX::1 269.804 ms 262.395 ms 257.647 ms 2 2001:470:0:5d::1 285.519 ms 247.535 ms 267.457 ms 3 2001:504:f::18 268.754 ms 266.716 ms 255.840 ms 4 2001:4998:f023:204:: 257.244 ms 293.790 ms 2001:4998:f023:207:: 266.000 ms 5 2001:4998:f023:20b::1 265.909 ms 2001:4998:f023::1 285.568 ms 2001:4998:f023:203::1 269.768 ms 6 2001:4998:58:fc1a::1 275.205 ms 2001:4998:58:fe1e::1 265.732 ms 2001:4998:124:fc05::1 292.157 ms 7 2001:4998:58:fa09::1 259.627 ms 2001:4998:58:19f9::1 265.526 ms 2001:4998:58:fa09::1 285.432 ms 8 2001:4998:58:1836::10 270.869 ms 266.211 ms 265.356 ms |