I recently has upgraded the FreeBSD version to 13 and found that the IPSec site to site between FreeBSD 13 to Juniper SRX is not working anymore. Strongswan is ditching the ipsec.conf and move to swanctl.conf. If we are moving to the vici, this requires some effort to translate the config.
I have attached the quick and dirty sample to build a Policy based site to site IPSec vpn with Strongswan. Enhancement is required for production.
The sample is suitable for the following:
– policy based VPN
– using PSK.
– source vpn termination point is NATTed and behind a internet gateway.
– dynamic public IP address for source vpn termination point.
– dynamic destination IP address for the remote IPSec VPN termination point. (required the DNS lookup for the source vpn termination point.)
– multiple VPN termination points from the same source public IP address are allowed.
Install the Strongswan into the FreeBSD:
pkg install strongswan The default strongSwan configuration interface have been updated to vici since version 5.9.2_1. To use the stroke interface by default either compile the port without the vici option or set 'strongswan_interface="stroke"' in your rc.conf file.
The swanctl config is located as listed below:
/usr/local/etc/swanctl/conf.d # ls FBSD-AJ1401SRX01.conf /usr/local/etc/swanctl/conf.d # vi FBSD-AJ1401SRX01.conf
Add the following into the /etc/rc.conf
##### enable strongswan for IPSec VPN ##### /usr/local/etc. Edit ipsec.conf strongswan_enable="YES" ########################
Once the config file is completed, then reset the service.
service strongswan restart
connections {
AJ1401SRX01 {
aggressive = yes
remote_addrs = <ip address or domain name>
# if using domain then the machine needs to be able to perform DNS lookup.
version = 1
# using ikev1 only.
proposals = <same format as the ipsec.conf>
local-1 {
auth = psk
id = AJHKGMATFWL01.ddns.sample
# this is the local identity using hostname
}
remote-1 {
id = fatball.ddns.sample
# this is the remote identity using hostname
auth = psk
}
children {
# this is the phase 2 section.
AJ1401SRX01-1 {
local_ts = 172.16.254.13/32
remote_ts = 172.16.254.12/32
# the lines above are the interested traffic for policy based vpn.
esp_proposals = <same format as the ipsec.conf>
start_action = trap
dpd_action = restart
}
}
}
}
secrets {
ike-AJ1401SRX01 {
secret = "the_PSK_secret_of_the_tunnel"
id-1 = fatball.ddns.sample
}
}The following command can be used for troubleshooting and checking:
swanctl –list-conns
# this lists out the loaded config.
swanctl –log
# this gives you the error log for live troubleshoot.
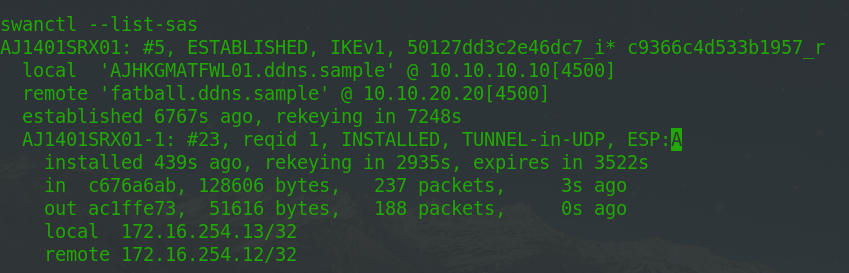
swanctl –list-sas
# this lists out the connected tunnel.
Allow to use aggressive mode with PSK.
vi /usr/local/etc/strongswan.conf
add the following.
i_dont_care_about_security_and_use_aggressive_mode_psk = yes Reference:
– Strongswan ipsec.conf to swanctl.conf migration sample.
https://wiki.strongswan.org/projects/strongswan/wiki/Fromipsecconf
– Strongswan sample.
https://wiki.strongswan.org/projects/strongswan/wiki/UsableExamples
– Cipher options.
https://wiki.strongswan.org/projects/strongswan/wiki/IKEv1CipherSuites
https://wiki.strongswan.org/projects/strongswan/wiki/IKEv2CipherSuites
– allow aggressive mode with PSK in Strongswan.
error message: Aggressive Mode PSK disabled for security reasons
https://support.fortinet.com.cn/uploadfile/wangxiang/IPSEC%20VPN%20_between_Strongswan_and_FGT.pdf