Setting up a policy based site to site IPSec VPN tunnel with static IP address is quite stright forward in Cisco ASA, but what if one of the end point is using dymanic IP address?
In this lab, I will be using 2 virtual ASA (9.6(2)) to create a site to site IPSec VPN tunnel, as well as setting up Cisco VPN client in one of the ASA with static IP address.
The ASA-F14 is the one with static IP address, and the ASA-F16 is using dynamic IP address.
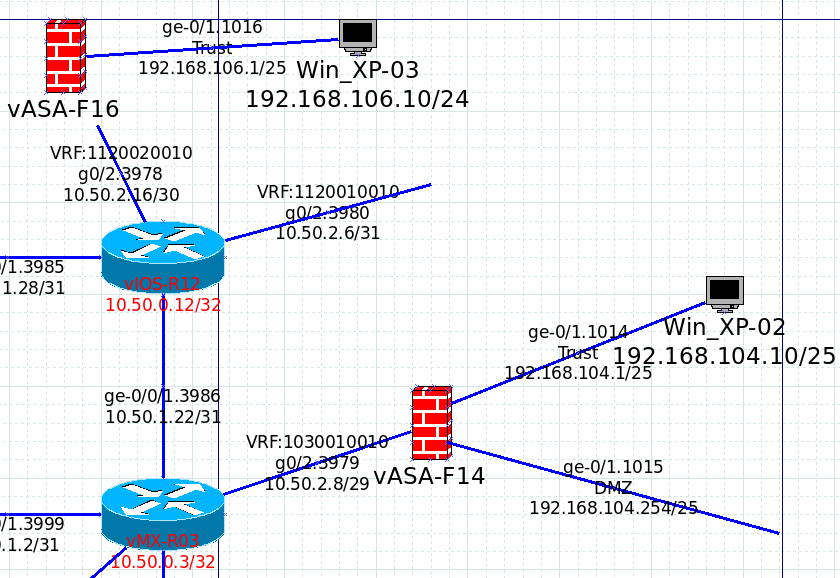
Let s take a look at the IP address of ASA-F14 and ASA-F16.
| net-vASA-AS5052-F14# sho ip |
| System IP Addresses: Interface Name IP address Subnet mask Method GigabitEthernet0/0.3979 untrust 10.50.2.10 255.255.255.248 manual GigabitEthernet0/1.1014 trust 192.168.104.1 255.255.255.128 manual |
| net-AS5052-vASA-F16# sho ip |
| System IP Addresses: Interface Name IP address Subnet mask Method GigabitEthernet0/0.3978 untrust 10.50.2.18 255.255.255.252 manual GigabitEthernet0/2.1016 trust 192.168.106.1 255.255.255.128 manual |
Let s take a look at the configuration in ASA-F14 and ASA-F16 below.
– ASA-F14 has included the site to site IPSec vpn and the remote vpn syntax.
– ASA-F16 has a set of site to site IPSec VPN syntax only.
– Highlighted objects need to pay attentions to for creating L2L VPN with dynamic address.
– the related tunnel syntax are putting side by side for easy of comparison.
| ASA-F14 (with static IP address) | ASA-F16 (with dynamic IP address) |
| ip local pool ciscovpn_pool 192.168.0.10-192.168.0.15 access-list testgroup_splitTunnel standard permit 192.168.104.0 255.255.255.128 |
|
| group-policy testgroup internal group-policy testgroup attributes dns-server value 1.2.3.4 vpn-tunnel-protocol ikev1 split-tunnel-policy tunnelspecified split-tunnel-network-list value testgroup_splitTunnel default-domain value testgroup.local |
|
| username netuser password ayQxwgFdIr4e4PXC encrypted privilege 15 |
|
| crypto isakmp identity key-id VPN_F14-F16 (this is to identify the firewall itself as the name that match with the end point s tunnel group name.) |
|
| tunnel-group VPN_F14-F16 type ipsec-l2l tunnel-group VPN_F14-F16 ipsec-attributes ikev1 pre-shared-key 123456 (The tunnel name for dynamic address end point is similar with Cisco remote access) |
tunnel-group 10.50.2.10 type ipsec-l2l tunnel-group 10.50.2.10 ipsec-attributes ikev1 pre-shared-key 123456 (The tunnel configuration in ASA-F16 does not have anything special) |
| tunnel-group testgroup type remote-access tunnel-group testgroup general-attributes address-pool ciscovpn_pool default-group-policy testgroup tunnel-group testgroup ipsec-attributes ikev1 pre-shared-key cisco123 |
|
| crypto dynamic-map cisco_remote_vpn 5 set ikev1 transform-set ESP-3DES-MD5 crypto dynamic-map cisco_remote_vpn 5 set reverse-route |
|
| crypto dynamic-map L2L-dynamic_IP 5 match address vpn-F14_to_F16 crypto dynamic-map L2L-dynamic_IP 5 set ikev1 transform-set ESP-3DES-MD5 |
|
| crypto map vpn 65530 ipsec-isakmp dynamic L2L-dynamic_IP (The L2L vpn is slightly higher than the Cisco VPN client profile) |
crypto map vpn 50 match address vpn-F16_to_F14 crypto map vpn 50 set peer 10.50.2.10 crypto map vpn 50 set ikev1 phase1-mode aggressive crypto map vpn 50 set ikev1 transform-set ESP-3DES-MD5 |
| crypto map vpn 65535 ipsec-isakmp dynamic cisco_remote_vpn |
|
| crypto map vpn interface untrust crypto ikev1 enable untrust |
crypto map vpn interface untrust crypto ikev1 enable untrust |
| crypto ikev1 policy 1 authentication pre-share encryption 3des hash sha group 2 lifetime 86400 crypto ikev1 policy 10 authentication pre-share encryption des hash sha group 2 lifetime 86400 |
crypto ikev1 policy 1 authentication pre-share encryption 3des hash sha group 2 lifetime 86400 crypto ikev1 policy 10 authentication pre-share encryption des hash sha group 2 lifetime 86400 |
| access-list vpn-F14_to_F16 extended permit ip 192.168.104.0 255.255.255.0 192.168.106.0 255.255.255.128 |
access-list vpn-F16_to_F14 extended permit ip 192.168.106.0 255.255.255.128 192.168.104.0 255.255.255.0 |
The testing result:
The ikev1 sa:
Since ASA-F16 does not have static IP address, the tunnel will be always initial right from F16 to F14, which is similar with the Cisco vpn client.
| net-vASA-AS5052-F14# show crypto ikev1 sa | net-vASA-AS5052-F16# show crypto ikev1 sa |
| IKEv1 SAs: Active SA: 2 Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey) Total IKE SA: 2 1 IKE Peer: 10.50.2.18 Type : L2L Role : responder Rekey : no State : AM_ACTIVE 2 IKE Peer: 192.168.109.10 Type : user Role : responder Rekey : no State : AM_ACTIVE |
IKEv1 SAs: Active SA: 1 Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey) Total IKE SA: 1 1 IKE Peer: 10.50.2.10 Type : L2L Role : initiator Rekey : no State : AM_ACTIVE |
The ipsec sa from both ASA.
| net-vASA-AS5052-F14# sho crypto ipsec sa |
net-AS5052-vASA-F16# sho crypto ipsec sa |
| interface: untrust Crypto map tag: L2L-dynamic_IP, seq num: 5, local addr: 10.50.2.10access-list vpn-F14_to_F16 extended permit ip 192.168.104.0 255.255.255.0 192.168.106.0 255.255.255.128 local ident (addr/mask/prot/port): (192.168.104.0/255.255.255.0/0/0) remote ident (addr/mask/prot/port): (192.168.106.0/255.255.255.128/0/0) current_peer: 10.50.2.18#pkts encaps: 36168, #pkts encrypt: 36168, #pkts digest: 36168 #pkts decaps: 36168, #pkts decrypt: 36168, #pkts verify: 36168 #pkts compressed: 0, #pkts decompressed: 0 #pkts not compressed: 36168, #pkts comp failed: 0, #pkts decomp failed: 0 #pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0 #PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0 #TFC rcvd: 0, #TFC sent: 0 #Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0 #send errors: 0, #recv errors: 0local crypto endpt.: 10.50.2.10/0, remote crypto endpt.: 10.50.2.18/0 path mtu 1500, ipsec overhead 58(36), media mtu 1500 PMTU time remaining (sec): 0, DF policy: copy-df ICMP error validation: disabled, TFC packets: disabled current outbound spi: 19C913BD current inbound spi : B6018C1Cinbound esp sas: spi: 0xB6018C1C (3053554716) transform: esp-3des esp-md5-hmac no compression in use settings ={L2L, Tunnel, IKEv1, } slot: 0, conn_id: 540672, crypto-map: L2L-dynamic_IP sa timing: remaining key lifetime (kB/sec): (3912880/10092) IV size: 8 bytes replay detection support: Y Anti replay bitmap: 0xFFFFFFFF 0xFFFFFFFF outbound esp sas: spi: 0x19C913BD (432608189) transform: esp-3des esp-md5-hmac no compression in use settings ={L2L, Tunnel, IKEv1, } slot: 0, conn_id: 540672, crypto-map: L2L-dynamic_IP sa timing: remaining key lifetime (kB/sec): (3912880/10092) IV size: 8 bytes replay detection support: Y Anti replay bitmap: 0x00000000 0x00000001 |
interface: untrust Crypto map tag: vpn, seq num: 50, local addr: 10.50.2.18access-list vpn-F16_to_F14 extended permit ip 192.168.106.0 255.255.255.128 192.168.104.0 255.255.255.0 local ident (addr/mask/prot/port): (192.168.106.0/255.255.255.128/0/0) remote ident (addr/mask/prot/port): (192.168.104.0/255.255.255.0/0/0) current_peer: 10.50.2.10#pkts encaps: 36041, #pkts encrypt: 36041, #pkts digest: 36041 #pkts decaps: 36041, #pkts decrypt: 36041, #pkts verify: 36041 #pkts compressed: 0, #pkts decompressed: 0 #pkts not compressed: 36041, #pkts comp failed: 0, #pkts decomp failed: 0 #pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0 #PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0 #TFC rcvd: 0, #TFC sent: 0 #Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0 #send errors: 0, #recv errors: 0local crypto endpt.: 10.50.2.18/0, remote crypto endpt.: 10.50.2.10/0 path mtu 1500, ipsec overhead 58(36), media mtu 1500 PMTU time remaining (sec): 0, DF policy: copy-df ICMP error validation: disabled, TFC packets: disabled current outbound spi: B6018C1C current inbound spi : 19C913BDinbound esp sas: spi: 0x19C913BD (432608189) transform: esp-3des esp-md5-hmac no compression in use settings ={L2L, Tunnel, IKEv1, } slot: 0, conn_id: 503808, crypto-map: vpn sa timing: remaining key lifetime (kB/sec): (4371888/10156) IV size: 8 bytes replay detection support: Y Anti replay bitmap: 0xFFFFFFFF 0xFFFFFFFF outbound esp sas: spi: 0xB6018C1C (3053554716) transform: esp-3des esp-md5-hmac no compression in use settings ={L2L, Tunnel, IKEv1, } slot: 0, conn_id: 503808, crypto-map: vpn sa timing: remaining key lifetime (kB/sec): (4371888/10156) IV size: 8 bytes replay detection support: Y Anti replay bitmap: 0x00000000 0x00000001 |
| Crypto map tag: cisco_remote_vpn, seq num: 5, local addr: 10.50.2.10 local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0) remote ident (addr/mask/prot/port): (192.168.0.10/255.255.255.255/0/0) current_peer: 192.168.109.10, username: netuser dynamic allocated peer ip: 192.168.0.10 dynamic allocated peer ip(ipv6): 0.0.0.0 #pkts encaps: 25946, #pkts encrypt: 25946, #pkts digest: 25946 #pkts decaps: 25946, #pkts decrypt: 25946, #pkts verify: 25946 #pkts compressed: 0, #pkts decompressed: 0 #pkts not compressed: 25946, #pkts comp failed: 0, #pkts decomp failed: 0 #pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0 #PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0 #TFC rcvd: 0, #TFC sent: 0 #Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0 #send errors: 0, #recv errors: 0 local crypto endpt.: 10.50.2.10/0, remote crypto endpt.: 192.168.109.10/0 path mtu 1500, ipsec overhead 58(36), media mtu 1500 PMTU time remaining (sec): 0, DF policy: copy-df ICMP error validation: disabled, TFC packets: disabled current outbound spi: 8C8BE792 current inbound spi : 64FABA97 inbound esp sas: spi: 0x64FABA97 (1694153367) transform: esp-3des esp-md5-hmac no compression in use settings ={RA, Tunnel, IKEv1, } slot: 0, conn_id: 532480, crypto-map: cisco_remote_vpn sa timing: remaining key lifetime (sec): 25858 IV size: 8 bytes replay detection support: Y Anti replay bitmap: 0xFFFFFFFF 0xFFFFFFFF outbound esp sas: spi: 0x8C8BE792 (2357979026) transform: esp-3des esp-md5-hmac no compression in use settings ={RA, Tunnel, IKEv1, } slot: 0, conn_id: 532480, crypto-map: cisco_remote_vpn sa timing: remaining key lifetime (sec): 25858 IV size: 8 bytes replay detection support: Y Anti replay bitmap: 0x00000000 0x00000001 |
Ping test:
The ASA-F16 shows the 192.168.106.10 can ping to 192.168.104.10.
The ASA-F14 shows the both L2L VPN and remote vpn can ping to 192.168.104.10.
| net-AS5052-vASA-F16# sho conn | in ICMP ICMP untrust 192.168.104.10:0 trust 192.168.106.10:512, idle 0:00:00, bytes 72736, flags ICMP untrust 192.168.104.10:512 trust 192.168.106.10:0, idle 0:00:00, bytes 72896, flags |
| net-vASA-AS5052-F14# sho conn | in ICMP ICMP untrust 192.168.0.10:768 trust 192.168.104.10:0, idle 0:00:00, bytes 916384, flags ICMP untrust 192.168.106.10:512 trust 192.168.104.10:0, idle 0:00:00, bytes 92672, flags |
From the lab above, it shows the ASA to run the IPSec VPN with dynamic IP address does not have any issue. Plus, it can co-operate with the Cisco vpn client.
Is it okay if I ask you to clear up some misconceptions? Could you show another example? Thank you!
hi, what are the misconceptions??