When testing firewalls ability against the DoS and session limit, there is a program in Linux called hping3 to produce flooding with. It can generate a small amount of packet flood while still keeping at lease 50% of CPU free for management.
if we need to test a session limit or threshold limit for SYNC flood toward to a web server port 80, we could use the command below.

# hping3 -i u1 -S -p 80 172.16.1.5
-S – indicates SYN flag
-p 80 – Target port 80
-i u1 – Wait for 1 micro second between each packet
Based of the result below, we can see hping3 is generate a TCP type of packet and sending traffic to port 80 of 172.16.1.5 as destination. You can pay a little attention on the time frame as well.
| 21:28:02.108024 IP (tos 0x0, ttl 64, id 30525, offset 0, flags [none], proto TCP (6), length 40) 172.16.2.18.15513 > 172.16.1.5.80: Flags [S], cksum 0x9967 (correct), seq 652361374, win 512, length 0 21:28:02.108067 IP (tos 0x0, ttl 64, id 15118, offset 0, flags [none], proto TCP (6), length 40) 172.16.2.18.15514 > 172.16.1.5.80: Flags [S], cksum 0x7024 (correct), seq 1361228312, win 512, length 0 21:28:02.108123 IP (tos 0x0, ttl 64, id 61360, offset 0, flags [none], proto TCP (6), length 40) 172.16.2.18.15515 > 172.16.1.5.80: Flags [S], cksum 0x471a (correct), seq 651571276, win 512, length 0 21:28:02.108180 IP (tos 0x0, ttl 64, id 10258, offset 0, flags [none], proto TCP (6), length 40) 172.16.2.18.15516 > 172.16.1.5.80: Flags [S], cksum 0x6af3 (correct), seq 954783411, win 512, length 0 21:28:02.108235 IP (tos 0x0, ttl 64, id 20246, offset 0, flags [none], proto TCP (6), length 40) 172.16.2.18.15517 > 172.16.1.5.80: Flags [S], cksum 0xae73 (correct), seq 254599339, win 512, length 0 21:28:02.108298 IP (tos 0x0, ttl 64, id 48823, offset 0, flags [none], proto TCP (6), length 40) 172.16.2.18.15518 > 172.16.1.5.80: Flags [S], cksum 0xbdc9 (correct), seq 1616407911, win 512, length 0 21:28:02.108375 IP (tos 0x0, ttl 64, id 11273, offset 0, flags [none], proto TCP (6), length 40) ^C 172.16.2.18.15519 > 172.16.1.5.80: Flags [S], cksum 0x1cf2 (correct), seq 1226450215, win 512, length 0 |
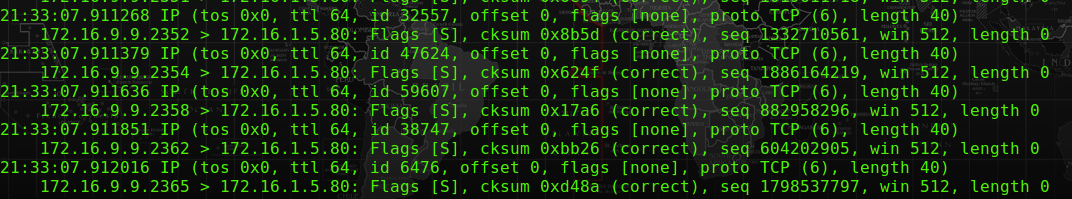
But in the case if we want to spoof the source address with another address, then we can use the paramater of “-a”. With the command below, it will send packets to 172.16.1.5 on behalf of 172.16.9.9
# hping3 -i u1 -S -p 80 172.16.1.5 -a 172.16.9.9
-a – to amend the source address of the packets
| 21:33:07.911051 IP (tos 0x0, ttl 64, id 3061, offset 0, flags [none], proto TCP (6), length 40) 172.16.9.9.2349 > 172.16.1.5.80: Flags [S], cksum 0xde0b (correct), seq 1951941470, win 512, length 0 21:33:07.911124 IP (tos 0x0, ttl 64, id 21261, offset 0, flags [none], proto TCP (6), length 40) 172.16.9.9.2350 > 172.16.1.5.80: Flags [S], cksum 0xc771 (correct), seq 1069435591, win 512, length 0 21:33:07.911200 IP (tos 0x0, ttl 64, id 55266, offset 0, flags [none], proto TCP (6), length 40) 172.16.9.9.2351 > 172.16.1.5.80: Flags [S], cksum 0x6e94 (correct), seq 1019611718, win 512, length 0 21:33:07.911268 IP (tos 0x0, ttl 64, id 32557, offset 0, flags [none], proto TCP (6), length 40) 172.16.9.9.2352 > 172.16.1.5.80: Flags [S], cksum 0x8b5d (correct), seq 1332710561, win 512, length 0 21:33:07.911379 IP (tos 0x0, ttl 64, id 47624, offset 0, flags [none], proto TCP (6), length 40) 172.16.9.9.2354 > 172.16.1.5.80: Flags [S], cksum 0x624f (correct), seq 1886164219, win 512, length 0 21:33:07.911636 IP (tos 0x0, ttl 64, id 59607, offset 0, flags [none], proto TCP (6), length 40) 172.16.9.9.2358 > 172.16.1.5.80: Flags [S], cksum 0x17a6 (correct), seq 882958296, win 512, length 0 21:33:07.911851 IP (tos 0x0, ttl 64, id 38747, offset 0, flags [none], proto TCP (6), length 40) 172.16.9.9.2362 > 172.16.1.5.80: Flags [S], cksum 0xbb26 (correct), seq 604202905, win 512, length 0 21:33:07.912016 IP (tos 0x0, ttl 64, id 6476, offset 0, flags [none], proto TCP (6), length 40) 172.16.9.9.2365 > 172.16.1.5.80: Flags [S], cksum 0xd48a (correct), seq 1798537797, win 512, length 0 |
Hping3 has more advance feature of packet crafting. I hope the info above can give you a general idea of how we can use hping3 for testing your environment or your firewall settings. I will share some more advance or other features in the coming future.
!!!! Please do no perform hping testing without permission.!!!
!!!! Also, do no perform address spoofing behind any NAT devices, as the packet arrives to the destination will be using the source address of your public ip address.!!!!