How yall doing guys. It has been some times putting anything new to my blog. I think I will put some more materials that focus on troubleshooting wise stuffs. This time, I will present the way to check the label switching path or routing path of the MPLS VPN traffic that run on top of the OSPF and LDP protocols.
Here is the Topology. The lab is build with both Cisco IOS (C1000v) and JunOS. There is 2 subnets in the VRF which are 192.168.104.0/24 and 192.168.109.0/24 and they are located in the R3 and R10 respectively.

Continue reading
Category Archives: Computer Networking
Networking – layer 2 communication.
Compute networking sometimes gives new ITers a feeling of confusion and complication when they start learning networking, this post will simply explain it in laymen terms and provide a basic concept and some basic configuration on Cisco productions for reference.
So what is layer 2 communication? What does it provide or allow us to do? What is networking HUB and what can it do? What is the different between network switches? What are LAN and what are VLANs? (This post will explain the ethernet network only) Continue reading
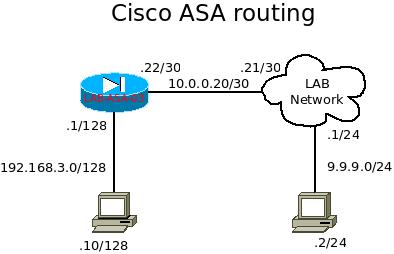
Cisco ASA – routing sample
In this post, I will show you guys how to setup a Cisco ASA firewall serves as a layer 3 packet transfer device. The example will be demonstrate with 192.168.3.10/32 machine accessing to 9.9.9.92/32 via IPerf. There is only simple routing and has no NAT involve.
In this setup, the ASA is acting as the gateway between office network and the internet. The 192.168.3.0/24 is the internal subnet and 10.0.0.20/30 is the internet. There are couple areas we have to handle, and they are routing, and policy. Since ASA is a stateful device, we have to apply policy to allow internal network to access external network, but not vise versa.
Continue reading
Cisco ASA – Checking information
Cisco ASA firewall is a security appliance that can perform packet inspection and with limited routing features. For those who are new to this product, it uses different ways to present its information than Cisco routers. There might have some difficulty at first, but since it is using syntax similar with other Cisco products, such as “show run”, and it is not too hard to pick up this product. I will list out some frequently used commands for troubleshooting purpose.
- show run – this is to show the running configuration the cisco ASA is running with.
- show run all – this is to show the configuration users had input and as well the default settings that is being run by the ASA.
- show ip – this is similar with the “sho ip int br” from other Cisco products, and it displays the address information being set in the ASA.
- show nameif – this is to show the association of the interfaces and the “zone”. This “zone” used for differentiate the purpose of each interface, such as “DMZ”, “inside”, “outside”, and etc…
- show xlate – this is to show the NAT information with the translated flow. It shares some information with “show nat” too.
- show nat – similar with “show xlate”.
- show conn – it can be used to show sessions with.
- show version – it shows the information of the ASA, including RAM, CPU, serial number of the device, uptime, and license information.
- show crypto ikev1 sa – to check the ikev1 active tunnels info.
- show crypto ikev2 sa – to check the ikev2 active tunnels info.
- show ipsec sa – it shows the ipsec active tunnels info.
- show interface – it shows information for the physical interfaces including the MAC address, BW, duplex, speed, as well as CRC errors.
Commands above are for general use, and can be run under “config mode” without the “do”. I will demonstrate more command within my ASA posts.
Using dynamic DNS at SRX with non DYNDNS service provider
When placing a network equipment without a static IP address, the best way to remote access to the device is by using the dynamic DNS service. Juniper has import this feature into their network security products such as Netscreen ScreenOS and JunOS SRX.
I recently has replaced my SSG with the SRX, and am having trouble updating the DDNS record with the built-in DDNS feature. What happen is SRX only offer 2 options of “dyndns.org or ddo.jp”, any service other than these 2 are out of questions. Since I am using HE.net for DDNS, that does not do my any good.

So my work around is: to map the dyndns domain name to a HE.net dns server IP address with the following command. The command below is to bind the members.dyndns.org (the dyndns.org DDNS service domain name) to the IP address of 184.105.242.3 (the DDNS service domain name). Continue reading
Turning Raspberry PI into WIFI AP (in bridge mode)

Turning raspberry PI into WIFI AP: SSG5 to SRX migration (part 2)
Due to the insecure of internet platform, I have decided to run a security appliance at home to replace my SSG firewall. My newest design is to have SRX as the SSG replacment. Since SRX lacks of the feature of build-in WIFI, I have decided to use RASPBERRY PI as the WIFI AP bridge to cover the wireless access feature. In part 2 of this migration, it mainly focus on turning the RASPBERRY PI as the WIFI AP and bridge it to its ETH0 interface.
The WIFI AP elements:
– Raspberry PI model B
– 0ace:1215 ZyDAS ZD1211B 802.11g
Design for PI:
– Since the ESXi host is using trunk, the PI needs to have its NIC ready to take tagged and untag packets.
– PI turns the WIFI NIC into WIFI access point
– PI needs to bridge the ETH NIC and WIFI NIC to extend the SRX LAN boardcast domain with wireless capability.
Continue reading
Traffic Engineering – MPLS
This time we will handle the basic traffic engineering within a MPLS network. This technique allows network admin to manipulate the traffic and fully utilize the subscribed bandwidth or circuits.
Traffic engineering within a MPLS network can be more accurate and convenience than in a typical TCP/IP network, because TE are happened at the MPLS level only, which would not affect the base of the whole network topology. If manipulate traffic at the IP level, everything running on top of IP level will be affected.
The network topology for this testing is listed below.
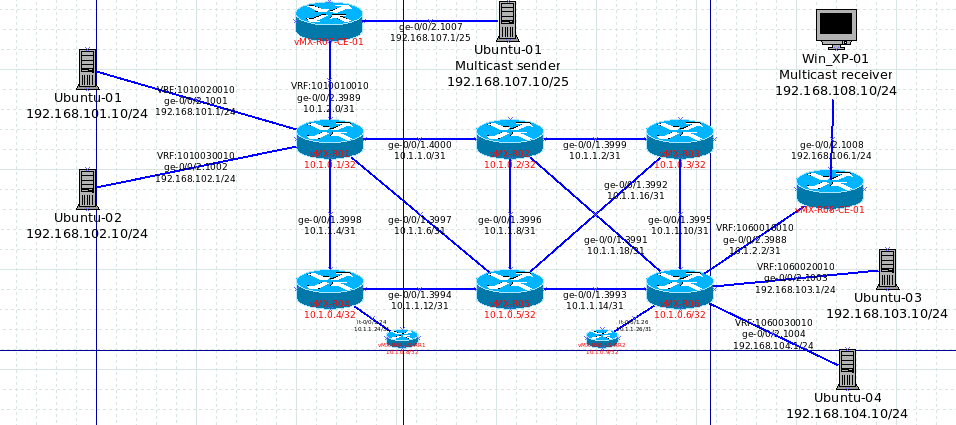
Continue reading
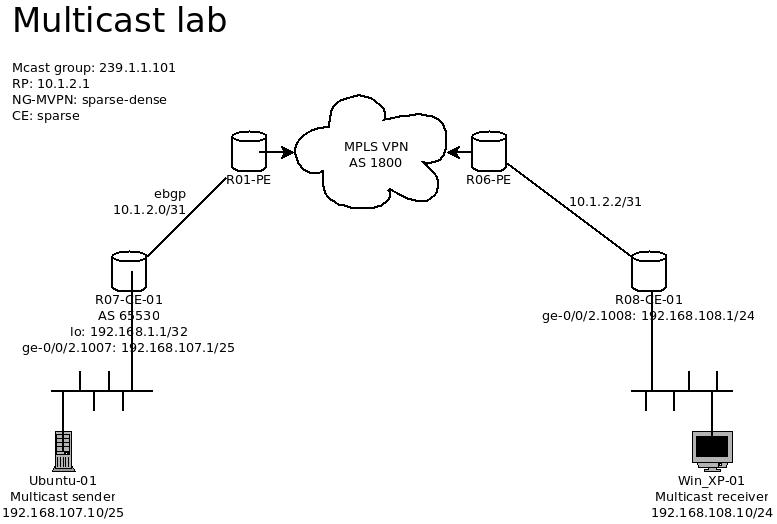
Playing with Multicast – Part 4 – NV-MVPN on Junos
It sure has been some times since the last multicast post. This time, we will put the lab into a higher level, and will be running the multicast on the MPLS VPN platform. Since this post is focusing on MCast only, the configuration for MPLS network will not be described with my detail. So let s dig in.
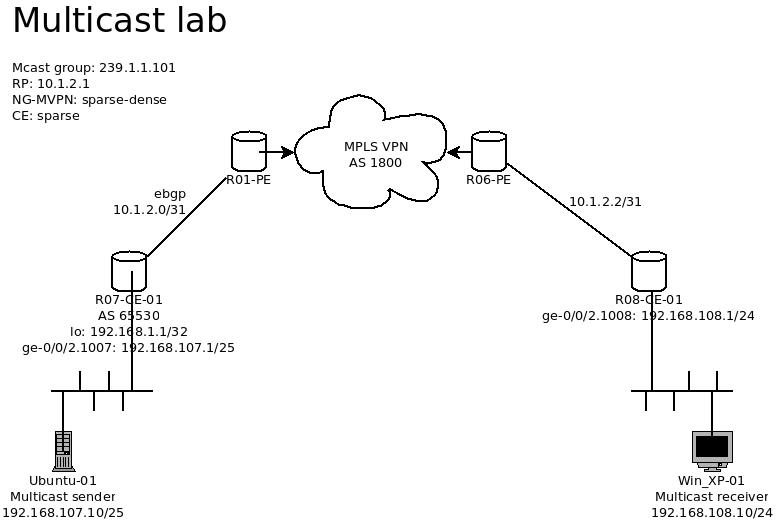
Continue reading
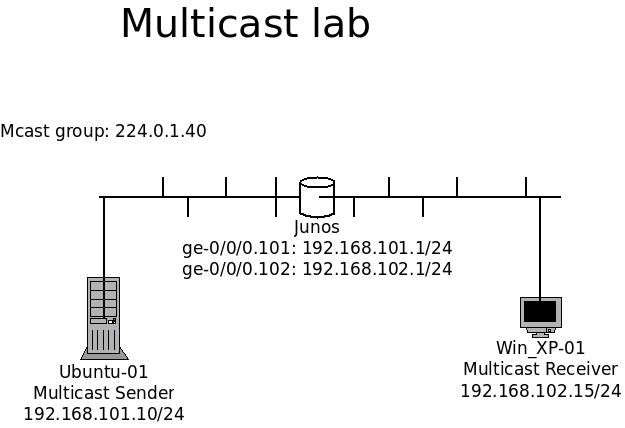
Playing with Multicast – Part 2.
The part 1 of multicast was simply doing the streaming within a local area network. This time, I will put my multicast lab to a level higher and put a router between the sender and receiver.
The test bed for this time will involve a simple routings. Please refer to the topology below.
To keep the multicast lab simple, it will be running on Sparse mode and using static RP instead of dynamic.
TOPOLOGY:
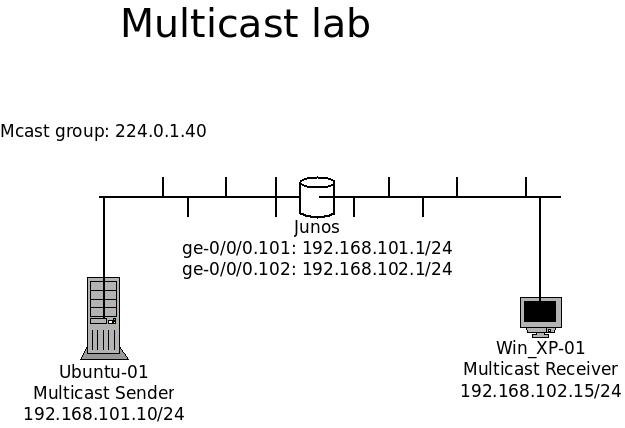
Components:
1x Ubuntus as sender
1x Windows XP as receiver.
1x Junos router Continue reading
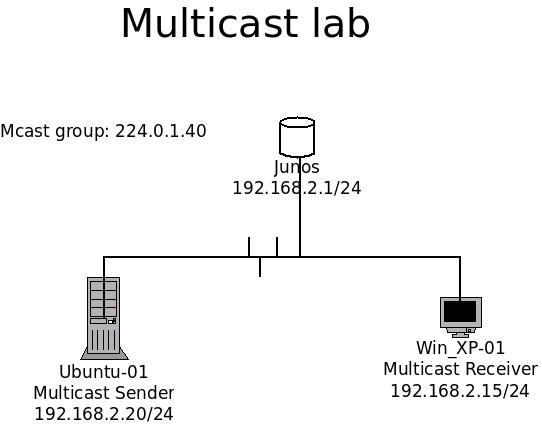
Playing with Multicast – Part 1.
It really has been a long time since my previous post. I have recently received a project that deal with multicast, a old technology that is really new to me.
I have been googling around for resources and references, and there are indeed a lot of results that mostly focus on theory. Therefore, I decided to contribute some of my hands on experiences for anyone who is building a similar lab as I do.
My lab builds from simple to complex (the difficulty is really based on my own experience only.) It starts from a playing multicast at a local area network and up to a MPLS VPN network.
Part 1 of the multicast post starts with 1x receiver and 1x sender in a local area network.
Part 2 of the multicast post is describes the lab with a router and one for each sender and receiver.
Part 3 of the multicast post is describes the lab with 3 routers and one for each sender and receiver.
(still organizing the information)
Part 4 of the multicast post is putting the lab from part 2 onto a MPLS VPN platform.
(still organizing the information)
Long story short, I will go straight to the part one deployment. The lab is simple; There is only 1 sender and 1 receiver within the same broadcast domain.
TOPOLOGY:

The Sender is an Ubuntu 14.04 32bit with updated components as of 2015 Dec,02. The receiver is a Win XP 32bit machine. Both of them are equipped with 512Mb of ram and 20G of hdd. Both machines are installed with VLC as for sending and receiving. There is a Junos device as their gateway, but it can be ignored for this lab since it does not have any PIM nor IGMP configured. Continue reading