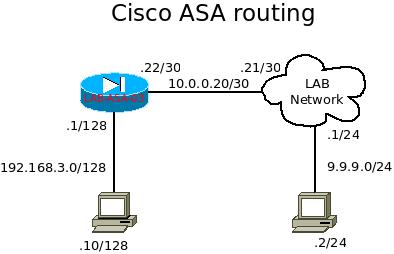
In this post, I will show you guys how to setup a Cisco ASA firewall serves as a layer 3 packet transfer device. The example will be demonstrate with 192.168.3.10/32 machine accessing to 9.9.9.92/32 via IPerf. There is only simple routing and has no NAT involve.
In this setup, the ASA is acting as the gateway between office network and the internet. The 192.168.3.0/24 is the internal subnet and 10.0.0.20/30 is the internet. There are couple areas we have to handle, and they are routing, and policy. Since ASA is a stateful device, we have to apply policy to allow internal network to access external network, but not vise versa.
First, we have to associate interfaces to a “zone”. In this case, the internal network will be called “inside” and external as “untrust”. The behavior of ASA by default will deny traffic flow from low security level zone to high security level zone. Therefore, when inside has level 100 and untrust with level 0, traffic from inside are allowed to untrust without additional policy.
interface GigabitEthernet0/2
nameif inside
security-level 100
ip address 192.168.3.1 255.255.255.0
interface GigabitEthernet0/0
nameif untrust
security-level 0
ip address 10.0.0.22 255.255.255.252
After applying the interface and ping to the peers, the arp records are listed below.
LAB-ASA-03# sho arp
untrust 10.0.0.21 000c.29ab.c69d 584
inside 192.168.3.10 000c.2953.a096 943
But as of this moment, the 192.168.3.10 still cannot access to the 9.9.9.2 because there is no route applied yet in the ASA. So we will setup a default gateway into the ASA to route the traffic from internal to external. The below command is to set the default route with the next hop of 10.0.0.21.
LAB-ASA-03# sho run route
route untrust 0.0.0.0 0.0.0.0 10.0.0.21
Once we have applied the default route, the 192.168.3.10 can iperf to 9.9.9.2. As listed in the “show conn” output, we can ensure there is a TCP connection initial from 192.168.3.10 to 9.9.9.2 s port 5001.
Final result:
LAB-ASA-03# sho conn
2 in use, 10 most used
TCP untrust 9.9.9.2:5001 inside 192.168.3.10:36712, idle 0:00:00, bytes 179232, flags UO
LAB-ASA-03# sho xlate
0 in use, 4 most used
Cisco ASA – routing sample
Leave a reply