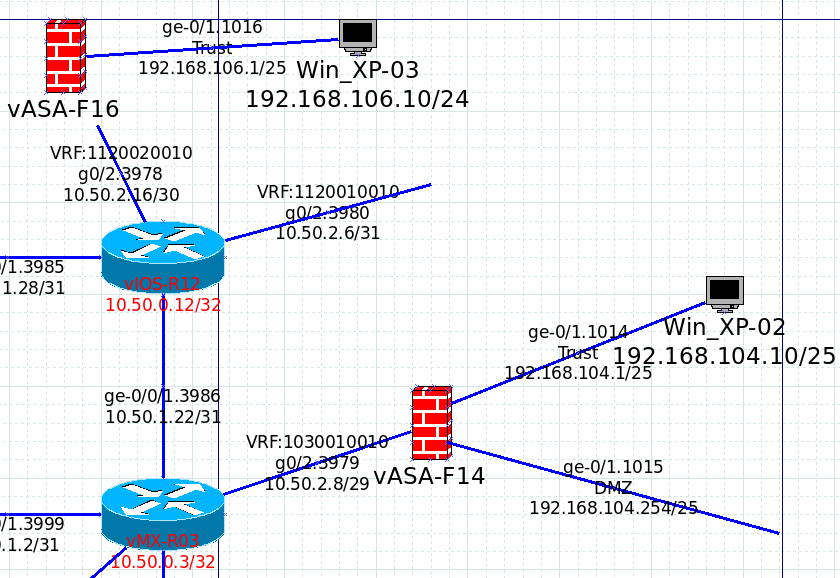
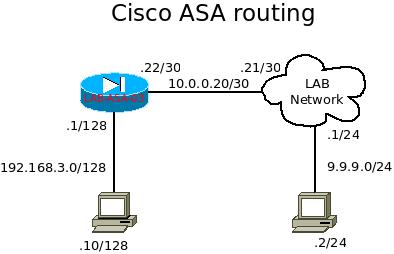
Cisco ASA firewall is a security appliance that can perform packet inspection and with limited routing features. For those who are new to this product, it uses different ways to present its information than Cisco routers. There might have some difficulty at first, but since it is using syntax similar with other Cisco products, such as “show run”, and it is not too hard to pick up this product. I will list out some frequently used commands for troubleshooting purpose.
- show run – this is to show the running configuration the cisco ASA is running with.
- show run all – this is to show the configuration users had input and as well the default settings that is being run by the ASA.
- show ip – this is similar with the “sho ip int br” from other Cisco products, and it displays the address information being set in the ASA.
- show nameif – this is to show the association of the interfaces and the “zone”. This “zone” used for differentiate the purpose of each interface, such as “DMZ”, “inside”, “outside”, and etc…
- show xlate – this is to show the NAT information with the translated flow. It shares some information with “show nat” too.
- show nat – similar with “show xlate”.
- show conn – it can be used to show sessions with.
- show version – it shows the information of the ASA, including RAM, CPU, serial number of the device, uptime, and license information.
- show crypto ikev1 sa – to check the ikev1 active tunnels info.
- show crypto ikev2 sa – to check the ikev2 active tunnels info.
- show ipsec sa – it shows the ipsec active tunnels info.
- show interface – it shows information for the physical interfaces including the MAC address, BW, duplex, speed, as well as CRC errors.
Commands above are for general use, and can be run under “config mode” without the “do”. I will demonstrate more command within my ASA posts.