The beaut of MPLS VPN is to have multi tenants running over the same MPLS core network and each tenant are prevented to access other tenants networks. But what if the 2 different tenants want to connect to each other?
In the lab below, we have 2 different tenants and they are 1120020010 (RT:200010) in Router 12 and 1030010010 (RT:100010) in Router 03. By default, the ASAs connected to these VRFs cannot communicate since they are in 2 different VRF network. In this case, I will be using Cisco IOS and Juniper MX to let 2 different VRFs to connect together.
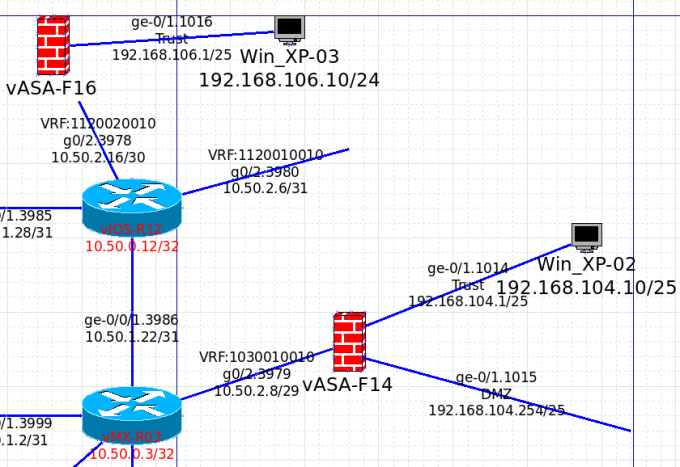
We could check the existing configuration and the route table in Router 03 and Router 12
In router 03, there are no 10.50.2.16/30 nor 192.168.106.0/25 in the VRF 1030010010 with the following configuration.
| set policy-options community 1030010010as5052 members target:5052:00100010 |
| set policy-options policy-statement 1030010010-export term 01-advertise from protocol direct set policy-options policy-statement 1030010010-export term 01-advertise from protocol static set policy-options policy-statement 1030010010-export term 01-advertise from protocol bgp set policy-options policy-statement 1030010010-export term 01-advertise then community add 1030010010as5052 set policy-options policy-statement 1030010010-export term 01-advertise then accept set policy-options policy-statement 1030010010-export term 99-reject then reject set policy-options policy-statement 1030010010-import term 01-receive from protocol bgp set policy-options policy-statement 1030010010-import term 01-receive from community 1030010010as5052 set policy-options policy-statement 1030010010-import term 01-receive then accept set policy-options policy-statement 1030010010-import term 99-reject then reject |
| set routing-instances 1030010010 instance-type vrf set routing-instances 1030010010 interface ge-0/0/2.3979 set routing-instances 1030010010 route-distinguisher 5052:1030010010 set routing-instances 1030010010 vrf-import 1030010010-import set routing-instances 1030010010 vrf-export 1030010010-export set routing-instances 1030010010 vrf-table-label set routing-instances 1030010010 routing-options static route 192.168.104.0/24 next-hop 10.50.2.10 set routing-instances 1030010010 routing-options router-id 10.50.2.9 |
| netuser@net-AS5052-vMX-R03> show route table 1030010010.inet.0 |
| 1030010010.inet.0: 9 destinations, 15 routes (9 active, 0 holddown, 0 hidden) + = Active Route, – = Last Active, * = Both10.50.2.0/31 *[BGP/170] 2d 12:33:43, localpref 100, from 10.50.0.8 AS path: I, validation-state: unverified > to 10.50.1.17 via ge-0/0/1.3992, Push 16, Push 422384(top) [BGP/170] 2d 12:33:43, localpref 100, from 10.50.0.9 AS path: I, validation-state: unverified > to 10.50.1.17 via ge-0/0/1.3992, Push 16, Push 422384(top) 10.50.2.2/31 *[BGP/170] 2d 18:01:11, localpref 100, from 10.50.0.8 AS path: I, validation-state: unverified > to 10.50.1.11 via ge-0/0/1.3995, Push 16 [BGP/170] 2d 18:01:11, localpref 100, from 10.50.0.9 AS path: I, validation-state: unverified > to 10.50.1.11 via ge-0/0/1.3995, Push 16 10.50.2.4/31 *[BGP/170] 2d 12:33:43, MED 0, localpref 100, from 10.50.0.8 AS path: ?, validation-state: unverified > to 10.50.1.17 via ge-0/0/1.3992, Push 43, Push 463904(top) [BGP/170] 2d 12:33:43, MED 0, localpref 100, from 10.50.0.9 AS path: ?, validation-state: unverified > to 10.50.1.17 via ge-0/0/1.3992, Push 43, Push 463904(top) 10.50.2.8/29 *[Direct/0] 6d 00:34:58 > via ge-0/0/2.3979 10.50.2.9/32 *[Local/0] 6d 00:34:58 Local via ge-0/0/2.3979 192.168.104.0/24 *[Static/5] 6d 00:34:58 > to 10.50.2.10 via ge-0/0/2.3979 192.168.107.0/25 *[BGP/170] 2d 12:33:43, localpref 100, from 10.50.0.8 AS path: 65530 I, validation-state: unverified > to 10.50.1.17 via ge-0/0/1.3992, Push 16, Push 422384(top) [BGP/170] 2d 12:33:43, localpref 100, from 10.50.0.9 AS path: 65530 I, validation-state: unverified > to 10.50.1.17 via ge-0/0/1.3992, Push 16, Push 422384(top) 192.168.108.0/24 *[BGP/170] 2d 18:01:11, localpref 100, from 10.50.0.8 AS path: I, validation-state: unverified > to 10.50.1.11 via ge-0/0/1.3995, Push 16 [BGP/170] 2d 18:01:11, localpref 100, from 10.50.0.9 AS path: I, validation-state: unverified > to 10.50.1.11 via ge-0/0/1.3995, Push 16 192.168.109.0/24 *[BGP/170] 2d 12:33:43, MED 0, localpref 100, from 10.50.0.8 AS path: ?, validation-state: unverified > to 10.50.1.17 via ge-0/0/1.3992, Push 42, Push 463904(top) [BGP/170] 2d 12:33:43, MED 0, localpref 100, from 10.50.0.9 AS path: ?, validation-state: unverified > to 10.50.1.17 via ge-0/0/1.3992, Push 42, Push 463904(top) |
In router 12, there are no 10.50.2.8/29 nor 192.168.104.0/24 in the VRF 1120020010 with the following configuration.
| vrf definition 1120020010 rd 5052:1120020010 route-target export 5052:200010 route-target import 5052:200010 ! address-family ipv4 exit-address-family |
| router bgp 5052 ! address-family ipv4 vrf 1120020010 redistribute connected neighbor 10.50.2.18 remote-as 65530 neighbor 10.50.2.18 activate exit-address-family ! |
| net-AS5052-vIOS-R12#sho ip route vrf 1120020010 |
| Routing Table: 1120020010 Gateway of last resort is not set10.0.0.0/8 is variably subnetted, 2 subnets, 2 masks C 10.50.2.16/30 is directly connected, GigabitEthernet0/2.3978 L 10.50.2.17/32 is directly connected, GigabitEthernet0/2.3978 B 192.168.101.0/24 [200/0] via 10.50.0.1, 20:01:19 B 192.168.103.0/24 [200/0] via 10.50.0.6, 20:01:19 192.168.106.0/25 is subnetted, 1 subnets B 192.168.106.0 [20/0] via 10.50.2.18, 19:14:02 |
So how do we get to have both ASA from 2 different VRFs to talk together? One of the quick and dirty way is to have 1120020010 to take routes from RT:100010 and to have 1030010010 to take RT:200010 routes. (A better way is to create a new RT and have both VRF to take routers from the new RT. But the idea is to break the VPN barrier here.)
| We will add a new command to have the VRF at router 12 to put routes from RT:100010 into its routing table. |
| vrf definition 1120020010 rd 5052:1120020010 route-target export 5052:200010 route-target import 5052:200010 route-target import 5052:100010 |
| net-AS5052-vIOS-R12#sho ip route vrf 1120020010 |
| Gateway of last resort is not set 10.0.0.0/8 is variably subnetted, 6 subnets, 4 masks B 10.50.2.0/31 [200/0] via 10.50.0.1, 00:06:40 B 10.50.2.2/31 [200/0] via 10.50.0.6, 00:06:40 B 10.50.2.4/31 [200/0] via 10.50.0.10, 00:06:40 B 10.50.2.8/29 [200/0] via 10.50.0.3, 00:06:40 C 10.50.2.16/30 is directly connected, GigabitEthernet0/2.3978 L 10.50.2.17/32 is directly connected, GigabitEthernet0/2.3978 B 192.168.101.0/24 [200/0] via 10.50.0.1, 20:17:16 B 192.168.103.0/24 [200/0] via 10.50.0.6, 20:17:16 B 192.168.104.0/24 [200/0] via 10.50.0.3, 00:06:40 192.168.106.0/25 is subnetted, 1 subnets B 192.168.106.0 [20/0] via 10.50.2.18, 19:29:59 192.168.107.0/25 is subnetted, 1 subnets B 192.168.107.0 [200/0] via 10.50.0.1, 00:06:40 B 192.168.108.0/24 [200/0] via 10.50.0.6, 00:06:40 B 192.168.109.0/24 [200/0] via 10.50.0.10, 00:06:40 |
Now we get to have all the routes from VRF RT:100010 in the 1120020010 VRF.
What about router 03? I will have the VRF 1030010010 to put all of the routes with RT:5052:200010 into its routing table. The newly imported routes are highlighted in red, and that both 192.168.106.0/25 and 10.50.2.16/30 are in the routing table.
| set policy-options community 1030020010as5052 members target:5052:00200010 |
| set policy-options policy-statement 1030010010-import term 01-receive from protocol bgp set policy-options policy-statement 1030010010-import term 01-receive from community 1030010010as5052 set policy-options policy-statement 1030010010-import term 01-receive from community 1030020010as5052 set policy-options policy-statement 1030010010-import term 01-receive then accept set policy-options policy-statement 1030010010-import term 99-reject then reject |
| netuser@net-AS5052-vMX-R03> show route table 1030010010.inet.0 |
| 1030010010.inet.0: 13 destinations, 23 routes (13 active, 0 holddown, 0 hidden) + = Active Route, – = Last Active, * = Both 10.50.2.0/31 *[BGP/170] 2d 13:37:39, localpref 100, from 10.50.0.8 AS path: I, validation-state: unverified > to 10.50.1.17 via ge-0/0/1.3992, Push 16, Push 422384(top) [BGP/170] 2d 13:37:39, localpref 100, from 10.50.0.9 AS path: I, validation-state: unverified > to 10.50.1.17 via ge-0/0/1.3992, Push 16, Push 422384(top) 10.50.2.2/31 *[BGP/170] 2d 19:05:07, localpref 100, from 10.50.0.8 AS path: I, validation-state: unverified > to 10.50.1.11 via ge-0/0/1.3995, Push 16 [BGP/170] 2d 19:05:07, localpref 100, from 10.50.0.9 AS path: I, validation-state: unverified > to 10.50.1.11 via ge-0/0/1.3995, Push 16 10.50.2.4/31 *[BGP/170] 2d 13:37:39, MED 0, localpref 100, from 10.50.0.8 AS path: ?, validation-state: unverified > to 10.50.1.17 via ge-0/0/1.3992, Push 43, Push 463904(top) [BGP/170] 2d 13:37:39, MED 0, localpref 100, from 10.50.0.9 AS path: ?, validation-state: unverified > to 10.50.1.17 via ge-0/0/1.3992, Push 43, Push 463904(top) 10.50.2.8/29 *[Direct/0] 6d 01:38:54 > via ge-0/0/2.3979 10.50.2.9/32 *[Local/0] 6d 01:38:54 Local via ge-0/0/2.3979 10.50.2.16/30 *[BGP/170] 00:00:11, MED 0, localpref 100, from 10.50.0.8 AS path: ?, validation-state: unverified > to 10.50.1.22 via ge-0/0/1.3986, Push 16 [BGP/170] 00:00:11, MED 0, localpref 100, from 10.50.0.9 AS path: ?, validation-state: unverified > to 10.50.1.22 via ge-0/0/1.3986, Push 16 192.168.101.0/24 *[BGP/170] 00:00:11, localpref 100, from 10.50.0.8 AS path: I, validation-state: unverified > to 10.50.1.17 via ge-0/0/1.3992, Push 17, Push 422384(top) [BGP/170] 00:00:11, localpref 100, from 10.50.0.9 AS path: I, validation-state: unverified > to 10.50.1.17 via ge-0/0/1.3992, Push 17, Push 422384(top) 192.168.103.0/24 *[BGP/170] 00:00:11, localpref 100, from 10.50.0.8 AS path: I, validation-state: unverified > to 10.50.1.11 via ge-0/0/1.3995, Push 17 [BGP/170] 00:00:11, localpref 100, from 10.50.0.9 AS path: I, validation-state: unverified > to 10.50.1.11 via ge-0/0/1.3995, Push 17 192.168.104.0/24 *[Static/5] 6d 01:38:54 > to 10.50.2.10 via ge-0/0/2.3979 192.168.106.0/25 *[BGP/170] 00:00:11, MED 0, localpref 100, from 10.50.0.8 AS path: 65530 ?, validation-state: unverified > to 10.50.1.22 via ge-0/0/1.3986, Push 41 [BGP/170] 00:00:11, MED 0, localpref 100, from 10.50.0.9 AS path: 65530 ?, validation-state: unverified > to 10.50.1.22 via ge-0/0/1.3986, Push 41 192.168.107.0/25 *[BGP/170] 2d 13:37:39, localpref 100, from 10.50.0.8 AS path: 65530 I, validation-state: unverified > to 10.50.1.17 via ge-0/0/1.3992, Push 16, Push 422384(top) [BGP/170] 2d 13:37:39, localpref 100, from 10.50.0.9 AS path: 65530 I, validation-state: unverified > to 10.50.1.17 via ge-0/0/1.3992, Push 16, Push 422384(top) 192.168.108.0/24 *[BGP/170] 2d 19:05:07, localpref 100, from 10.50.0.8 AS path: I, validation-state: unverified > to 10.50.1.11 via ge-0/0/1.3995, Push 16 [BGP/170] 2d 19:05:07, localpref 100, from 10.50.0.9 AS path: I, validation-state: unverified > to 10.50.1.11 via ge-0/0/1.3995, Push 16 192.168.109.0/24 *[BGP/170] 2d 13:37:39, MED 0, localpref 100, from 10.50.0.8 AS path: ?, validation-state: unverified > to 10.50.1.17 via ge-0/0/1.3992, Push 42, Push 463904(top) [BGP/170] 2d 13:37:39, MED 0, localpref 100, from 10.50.0.9 AS path: ?, validation-state: unverified > to 10.50.1.17 via ge-0/0/1.3992, Push 42, Push 463904(top) |
Here we come with the connection test.
We will ping from both ASA first.
| net-AS5052-vASA-F16# ping 10.50.2.10 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.50.2.10, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/4/10 ms |
| net-vASA-AS5052-F14# ping 10.50.2.18 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.50.2.18, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/10 ms |
Next, we will have the host behind the ASA to ping each other.
 |
 |
So at the end of the day, manipulating VRFs routes using RT (route target) can break the barrier and link 2 VRFs together. Although this is a quick and dirty way, an ideal way to create another RT and to add the RT into the routes that needs to be learned by another tenant s VRF for ease of management.